January 8, 2023

Ransomware is a type of malicious software (malware) that cybercriminals use to extort money from unsuspecting victims by locking them out of their data and threatening to delete it unless they pay a ransom. It typically spreads through email phishing scams, exploiting weaknesses in web browsers or operating systems, or using malicious links or downloads.
Ransomware works by first gaining access to the victim's computer, for which email fraud and phishing are the main tactics used. Scam mail masquerading as an email claiming to be legitimate often contain malicious attachments or links that can be clicked on to initiate an attack. Once the ransomware has gained access, it begins encrypting files on the system, making them unable to be opened or accessed without a decryption key. The ransomware then displays a message confirming the malicious attack by the scammers and demanding money for a key that will restore access to the data. Victims are often instructed to pay via cryptocurrency such as Bitcoin so they can remain anonymous while making payments.
Royal ransomware is one of many newer variants that have been distributed over recent months, primarily targeting entities within the U.S. however in recent months has started spreading to the UK and Europe as well. This new ransomware strain uses sophisticated techniques such as email phishing campaigns, email fraud and social engineering tactics to gain access to networks before surreptitiously encrypting all user files and asking for ransom payments in exchange for decrypting them again.
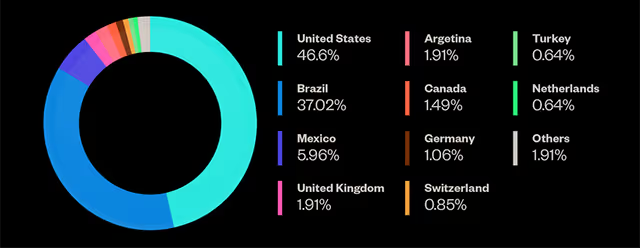
Royal Ransomware by Country - Source: Phishing Message
Royal ransomware was first spotted in January 2022, emerging as a new strain of malicious software that is being spread by cybercriminals from previous ransomware operations. Initially, Microsoft identified the threat and gave it the temporary name DEV-0569. However, researchers now believe that the criminals behind this ransomware are using Royal (the name left behind in recent ransom notes) as their official branding. It is primarily targeting entities within the United States and its tactics appear to include phishing email campaigns, social engineering tricks, malicious links, and dangerous downloads.
The ransomware works by first infiltrating its victims’ systems - a phishing message is the main technique used to gain access. Once inside the system, it begins to encrypt files so that they become inaccessible without a decryption key. The attackers then display a message demanding payment for the key to restoring data access. Victims are often instructed to pay via cryptocurrencies like Bitcoin to remain anonymous while making payments.
Ransomware is usually spread through phishing attacks that target vulnerable systems using malicious attachments, text messages and links. The malware is designed to gain access to the victim's system by exploiting weaknesses in email clients or web browsers, or by using malicious links or downloads. It then begins encrypting files on the network, making them inaccessible without a decryption key and displaying a message demanding payment for restoring access to them.
Ransomware typically leads to identity theft, lost money and overall financial loss. We highly advise organisations to have an active cyber security and a business interruption insurance policy in place with their insurance provider. Lyon Managed Services client success managers are highly trained and able to help with drawing together such policies.
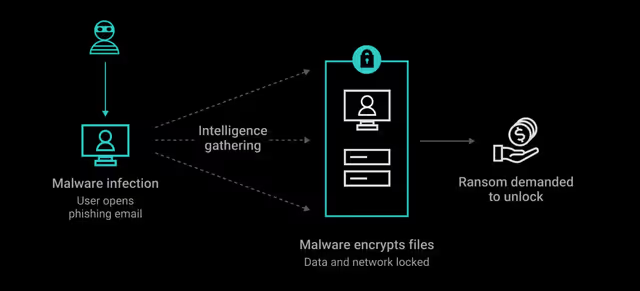
How ransomware spread through phishing emails and scam emails
Attackers will often confirm and establish an online chatroom where victims can contact them directly after receiving the ransom note, as well as offer help with data recovery if they cooperate in one-on-one sessions over chat platforms like Microsoft Teams or Discord. Other techniques attackers may use to gain access include social engineering tactics such as email spoofing, fraud and password brute forcing.
Additionally, some ransomware variants are programmed to spread across networks by exploiting insecure remote desktop protocol (RDP) connections and network shares. Once the ransomware has gained access, it starts to search for sensitive data such as documents, email archives and databases which are then encrypted before being exfiltrated from the compromised system. Victims are typically asked to pay a ransom in cryptocurrency like Bitcoin so they remain anonymous while making payments.
Furthermore, some ransomware attacks have been known to delete backups of sensitive information to increase pressure on victims into paying up. As a result, organisations need to ensure their data is backed up regularly and stored offline to prevent its loss should a ransomware attack occur.
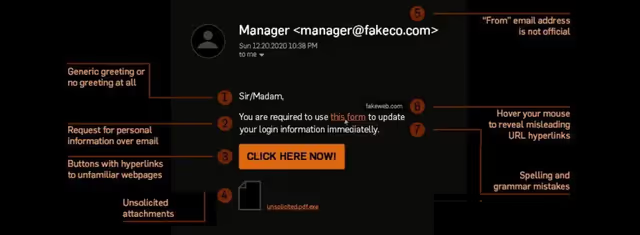
Email fraud is typically the most common initiator of ransomware
Phishing emails sent by scammers often appear to come from a legitimate source such as a bank, company, or government website. They typically contain links or attachments that direct users to malicious websites or download malicious content onto their devices. Identifying a phishing attack can be difficult as the perpetrators may use social engineering tactics to imitate an official entity. Some common signs of phishing emails include an urgent call for action, grammatical and spelling errors, requests for personal information, bank details, suspicious link or images, and an unfamiliar yet suspicious sender address.
To identify a scam email, it is important to monitor suspicious activity, closely examine the sender's address and look for any inconsistencies in the message’s content. Additionally, users should always be vigilant when it comes to opening files or clicking on URL's contained within these suspicious emails - even if they appear genuine - as this could result in malware being downloaded onto their devices.
Furthermore, users should never provide their login credentials or other personal information in response to an email request as this is often used by scammers to gain access to your account. Another key sign of a scam email is when its content appears too good to be true - such as offers of free services or products - as these are usually intended solely for collecting user data rather than actually providing any benefit.
A list of commonly reported suspicious emails typically include; Emails with urgent requests for action. Grammatical errors and spelling mistakes. Emails requesting payment information, bank details, account numbers, credit card numbers, offering money or claiming to offer a government refund. Requests for personal information. Emails from law enforcement partners, cyber crime agencies, London police or hosting companies. Suspicious link or text message. Emails that include a generic greeting from a familiar contact. Unfamiliar yet suspicious sending address. Different domain than the one used by the purported sender and their regular email address. Attached files that are not expected to form part of the email. Link directing to malicious websites. Offers of free services/products not intended to benefit the recipient.
One of the best ways to protect yourself from ransomware is to ensure that you and your organization are following best practices for cybersecurity. This includes keeping all software up-to-date with the latest security software patches, disabling unused services, setting strong passwords, enabling two-factor authentication, avoiding email attachments and links from unknown sources, and using a reliable antivirus program.
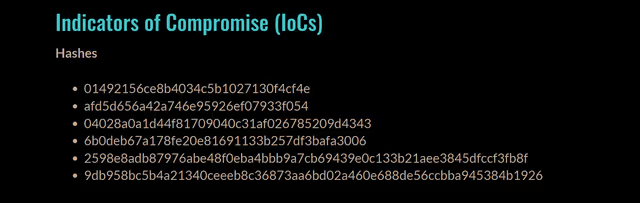
Royal Ransomware Hashes uploaded to infected system. Source: Phishing Email Scam
Additionally, it is important to be aware of the phishing email message received by the person that often accompanies ransomware attacks. Scam emails are typically sent in bulk by cyber criminals who have obtained email addresses or other personal or financial information of potential victims.
These phishing scam emails may contain malicious links that can be used to gain access to a network once opened. To defend against email phishing campaigns, email fraud and scam emails in general it is important for the person to always confirm the sender's email address before opening any suspect scam email message or clicking on any link. Organisations should also consider investing in advanced security solutions such as encryption software, email security and antivirus programs that can detect malicious files and malware infections before they can cause damage.
How royal ransomware typically spreads throughout the network
Additionally, organisations need to regularly backup sensitive data and store it offline in case of ransomware attacks. Furthermore, having an incident response plan in place should there be a breach can help reduce damage as well as restore operations quickly after an incident has occurred.
By following best practices for cybersecurity as well as staying informed about emerging threats from NCSC national cyber security centre, organisations can help reduce their chances of becoming victims of ransomware attacks!


